Bruter
by Worawit Wang
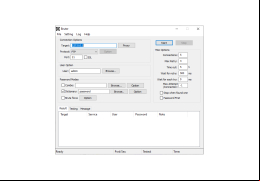
Bruter is a cracking tool designed to brute force credentials on remote services.
Bruter: Professional Cracking Software
Bruter is a professional -cracking software package designed to quickly and effectively crack s for various Windows, Linux, and Mac OS applications. Bruter has been designed to provide s with an easy-to-use, highly customizable, and powerful -cracking solution.
• s a range of common hashing algorithms
Bruter has the ability to a variety of common hashing algorithms, including MD5, SHA-1, SHA-2, and more. This allows s to quickly and easily crack s for the vast majority of applications.
• Automatically detects application type
Bruter is capable of automatically detecting the type of application the is attempting to crack the s for. This allows s to quickly and easily configure the software to suit their needs.
• Highly customizable
Bruter offers a wide range of customization options, allowing s to tailor the software to their specific needs. s can tweak settings, such as number of threads, dictionary size, and more.
• Multi-threaded
Bruter can utilize multiple threads to crack s faster and more efficiently. This allows s to crack multiple s in parallel, significantly reducing the time required to crack a .
• Dictionary attacks
Bruter can take advantage of dictionary attacks to crack s faster and more efficiently. Dictionary attacks allow s to quickly and easily crack s by attempting to match the against an existing list of known s.
• Brute-force attacks
In addition to dictionary attacks, Bruter can also utilize brute-force attacks to crack s. Brute-force attacks attempt to guess s by systematically trying every possible combination of characters.
• Automated cracking
Bruter can be used to automatically attempt to crack s. This allows s to set up automated cracking jobs, reducing the amount of time and effort required to crack a .
• Encrypted cracking
Bruter is capable of cracking s that are encrypted using a variety of algorithms. This allows s to quickly and easily crack s for a number of applications.
• Multi-platform
Bruter is designed to work with Windows, Linux, and Mac OS applications. This allows s to crack s for a variety of platforms, making it a versatile and powerful -cracking solution.
• Easy to use
Bruter has been designed to be easy to use, with a -friendly graphical interface. This allows s to quickly and easily configure Bruter to suit their needs and get cracking.
Bruter enables high-speed cracking of hash-based authentication systems.Features:
Bruter is a professional -cracking software package designed to quickly and effectively crack s for various Windows, Linux, and Mac OS applications. Bruter has been designed to provide s with an easy-to-use, highly customizable, and powerful -cracking solution.
• s a range of common hashing algorithms
Bruter has the ability to a variety of common hashing algorithms, including MD5, SHA-1, SHA-2, and more. This allows s to quickly and easily crack s for the vast majority of applications.
• Automatically detects application type
Bruter is capable of automatically detecting the type of application the is attempting to crack the s for. This allows s to quickly and easily configure the software to suit their needs.
• Highly customizable
Bruter offers a wide range of customization options, allowing s to tailor the software to their specific needs. s can tweak settings, such as number of threads, dictionary size, and more.
• Multi-threaded
Bruter can utilize multiple threads to crack s faster and more efficiently. This allows s to crack multiple s in parallel, significantly reducing the time required to crack a .
• Dictionary attacks
Bruter can take advantage of dictionary attacks to crack s faster and more efficiently. Dictionary attacks allow s to quickly and easily crack s by attempting to match the against an existing list of known s.
• Brute-force attacks
In addition to dictionary attacks, Bruter can also utilize brute-force attacks to crack s. Brute-force attacks attempt to guess s by systematically trying every possible combination of characters.
• Automated cracking
Bruter can be used to automatically attempt to crack s. This allows s to set up automated cracking jobs, reducing the amount of time and effort required to crack a .
• Encrypted cracking
Bruter is capable of cracking s that are encrypted using a variety of algorithms. This allows s to quickly and easily crack s for a number of applications.
• Multi-platform
Bruter is designed to work with Windows, Linux, and Mac OS applications. This allows s to crack s for a variety of platforms, making it a versatile and powerful -cracking solution.
• Easy to use
Bruter has been designed to be easy to use, with a -friendly graphical interface. This allows s to quickly and easily configure Bruter to suit their needs and get cracking.
The technical requirements for Bruter software depend on the specific version of the software being used. Generally, the system requirements for Bruter software include:
-A Windows or Linux operating system
-At least 2GB of RAM
-At least 100MB of free disk space
-A broadband internet connection
-An up-to-date graphics card
-The latest version of Java installed
-An up-to-date anti-virus program
-A Windows or Linux operating system
-At least 2GB of RAM
-At least 100MB of free disk space
-A broadband internet connection
-An up-to-date graphics card
-The latest version of Java installed
-An up-to-date anti-virus program
PROS
Easy to use with intuitive interface.
Effective for cracking tasks.
s multi-threading for faster operation.
Effective for cracking tasks.
s multi-threading for faster operation.
CONS
Interface can be quite complex for beginner s.
Limited customer options available.
Pricing can be considered high by some s.
Limited customer options available.
Pricing can be considered high by some s.
Jacob N.
I recently used the Bruter software for an online project. It was very easy to install and use, with a simple and intuitive interface. The software was also quite fast with its scanning capabilities, allowing me to get results in a timely manner. The cost of the software was also quite reasonable. On the downside, the software was a bit buggy and crashed a couple of times during my use. In addition, the customer seemed to be a bit slow in responding to my queries. All in all, it was a decent software for my needs.
Jay M********g
Bruter software is an effective tool for testing s. It is reliable and fast and can help you quickly identify weak s. It provides an easy way to check for possible combinations that can be used by hackers. Its interface is intuitive and straightforward. Setup and installation is quick and straightforward.
Sam X*********y
This software is a cracking tool that utilizes a brute-force attack to guess s. It is designed to be used by security professionals to test the strength of s and identify weaknesses in security systems. The software is highly customizable and allows s to set specific parameters for the attack, such as character sets and length. It also has the ability to pause and resume attacks, as well as save progress for future use.
Charlie
Powerful, efficient, -friendly -cracking tool.
Finn
Efficient cracking tool.
Reece
Bruter software helps crack s, it's super powerful!